SOC 2 compliance is an increasingly important topic for businesses that store and process customer data. SOC stands for “Service Organization Control”. While SOC 1 was designed specifically for internal controls, SOC 2 is an external assessment of a company’s management systems, which are used in assessing their ability to provide trustworthy services. One potential way to achieve SOC 2 compliance is to perform penetration tests on your company’s devices/IT infrastructure. But, before you can start thinking about SOC 2 penetration testing, it is important to first understand some key concepts about SOC 2.
What is SOC 2 compliance?

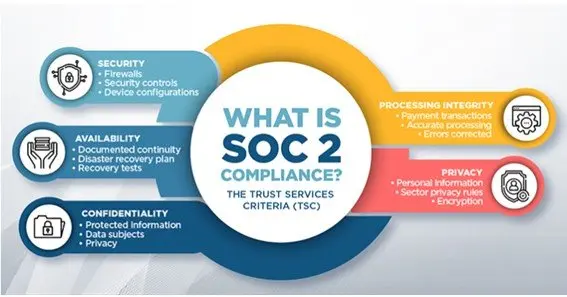
SOC 2 defines the criteria for an independent evaluation of a security program, typically through third-party assessments. It is usually unique to each company and covers a wide range of areas. However, it houses five core trust service principles and if you are looking for SOC 2 compliance then adhering to them is essential.
Also Read : How to prepare for a first interview
The 5 trust service principles of SOC 2
- Security: Adequate security measures should be in place to protect your company’s devices and IT infrastructure from unauthorized access. This can include both physical and digital security measures such as firewalls, intrusion detection, multi-factor authentication, CCTVs, etc.
- Availability: The system is operational whenever needed and functions as expected.
- Processing Integrity: System’s processing of data is complete, accurate and timely.
- Confidentiality: Sensitive information deemed to be confidential is protected during storage and disclosure (including transmission).
- Privacy: Individuals entitled to privacy receive notice of the information systems’ procedures regarding the protection of their personal information and have access to this data
Also Read : Explore Smart Conversion Copy Tricks for Attention-Grabbing & Engaging SEO Content
The difference between Type 1 and Type 2 examination in SOC 2

SOC 2 contains guidelines for the examination of organizations dealing with sensitive user data, specifically service organizations. SOC 2 reports should conclude how effectively operates with data. Furthermore, SOC 2 can be broken down into a Type 1 examination and a Type 2 examination, each a bit different from the other and to who should adhere to which may vary.
Click here – How to prepare for a first interview
SOC 2 Type 1
A SOC 2 Type 1 assessment focuses on SOC compliance and covers an organization’s internal controls. This SOC report is typically for company management, not the public.
SOC 2 Type 2
SOC 2 Type 2 assessments focus on SOC compliance and cover an organization’s policies, procedures, and controls. This SOC report covers how a company handles customer data.
Who should perform SOC 2 penetration testing?
The short answer is, any organization seeking to achieve or maintain SOC 2 compliance should consider performing penetration tests as part of their overall security program. However, SOC 2 penetration testing is especially important for organizations that process or store customer data, as this type of information is a prime target for attackers.
The next question that may arise is who should you turn to for penetration testing with this specific purpose in mind?
Who can carry out penetration tests for SOC 2 compliance?
A SOC 2 examination requires employees with experience in the SOC 2 field, and SOC 2 penetration testing is no exception. Penetration testers should be familiar with SOC 2 compliance guidelines to properly assess a company’s security. In addition, SOC 2 penetration tests require specific knowledge of how the organization works to find vulnerabilities that have been overlooked or not cared about by the business itself.
If IT security is not your company’s strong suit, then it is important to find an organization that can provide the necessary resources and knowledge to complete SOC 2 penetration tests.
Why is SOC 2 penetration testing important?
Security breaches are costly, both in terms of money and reputation. According to IBM’s Cost of a Data Breach Report 2021, the average cost of a data breach in 2021 was $161 per record accessed.
And so, the goal of performing web pen tests is clear. It aims at identifying vulnerabilities against your company’s devices/IT infrastructure that could be exploited by an attacker. This not only helps you to secure your systems but can also give you a better understanding of the risks associated with failing to be compliant with SOC 2 policies.
Importance of SOC 2 compliance:
- It provides a set of controls that can be used to protect an organization’s critical data.
- Not only for the sake of mandatory compliance in some industries, but it could also reflect the initiative taken by the company.
- SOC 2 reports are often requested by customers and partners as evidence of a good security posture.
- SOC 2 penetration testing can bring your attention to vulnerabilities before they are discovered by an outsider possibly with the intention of stealing your data. Hence, giving you time to fix them and prove to your consumers that you are indeed living up to the security measures you promised.
- By trying to achieve SOC 2 compliance you may uncover and be able to fix security weaknesses that were overlooked previously.
- If complying with SOC 2 is mandatory in your line of work, failing to do so may have serious consequences such as loss of customers, decreased trust, and more.
The SOC 2 compliance framework is vast and detailed, covering a wide range of security controls and requirements. However, it is important to remember that achieving SOC 2 compliance is not an end goal in itself – it’s simply a means to protect your organization from attacks and data breaches. And the best way to do that is by implementing a comprehensive security program, which should include SOC 2 penetration testing.
Conclusion
SOC 2 penetration testing is an important part of any security program and should be considered by any organization seeking SOC 2 compliance. By identifying vulnerabilities before they are exploited, you can get to fixing them immediately. You as well as your consumers stand to benefit from this. However, do bear in mind that simply achieving SOC 2 compliance may not be enough. Consider reaching out to a reputed cyber security company, especially one that specialises in SOC 2 compliance.
Click here – Explore Smart Conversion Copy Tricks for Attention-Grabbing & Engaging SEO Content